Shopify Integration Guide
How to detect and prevent fraudulent orders and account abuse on Shopify
When it comes to protecting your Shopify store from fraudulent activity, we analyze multiple data points to accurately assess risk. While email addresses provide early indicators of user intent, we also examine user purchase patterns, IP geolocation, device fingerprints, and behavioral signals. Orders from suspicious IP locations, unusual purchase patterns, or accounts using disposable email domains are often strongly correlated with fraud, abuse, or automated bots. By analyzing these comprehensive signals, you can proactively block bad actors before they place fraudulent orders or abuse your store's resources. In this guide, we'll walk through how to integrate TrustPath.io with your Shopify store to effectively reduce fraud and keep your business safe.
Prerequisites
1. One-Click Installation from Shopify App Store
The first step is to install the TrustPath Fraud Protection app from the Shopify App Store:
- Go to the Shopify App Store
- Click Add app
- Follow the installation prompts to connect your Shopify store.
TrustPath.io Threat Detection Rules
TrustPath.io threat detection rules are individual risk assessment criteria designed to identify and flag potentially fraudulent activity. Each rule evaluates specific signals—such as behavior patterns or metadata—to detect suspicious events and assigns a corresponding risk score.
The total risk score for an event ranges from 0 to 100, where:
- 0 indicates no risk (safe to approve)
- 100 indicates high risk (likely fraudulent, recommended to decline)
Default Fraud Detection Rules
To help you quickly identify and block high-risk orders, the following fraud detection rules are enabled by default:
Email-based Rules:
- Email address is disposable - Detects if the customer used a temporary or throwaway email service.
- Email is not deliverable - Checks if the email address cannot receive messages due to non-existent or unreachable inbox.
- Email server uses a Tor exit node - Flags if the email service is hosted on a known Tor network, often used to mask identity.
- Email server uses a proxy server - Identifies email servers behind anonymizing proxy infrastructure.
- Email address is invalid - Catches emails that are incorrectly formatted or syntactically invalid.
IP-based Rules:
- IP address is a Tor exit node - Flags orders placed through the Tor network, commonly used to conceal user location.
- IP address belongs to a data center - Detects usage of hosting providers, often linked to bots or scripted fraud attempts.
- IP address is associated with a proxy server - Identifies attempts to hide the true location of the user using proxies.
- IP address is known as a web crawler - Blocks orders from automated bots or scrapers posing as customers.
Location-based Rules:
- Billing country differs from shipping country - Flags when the billing and shipping addresses are in different countries—a common fraud red flag.
- Billing country differs from the IP location - Detects if the country tied to the billing info doesn't match the customer's current IP location.
Setting Up order_purchase Event
To configure further rules, that you wish consider, you can open TrustPath console by opening TrustPath app from Shopify admin UI and then clicking on the Open TrustPath.io Admin Panel:
That will take you to the https://console.trustpath.io/, once it is opened:
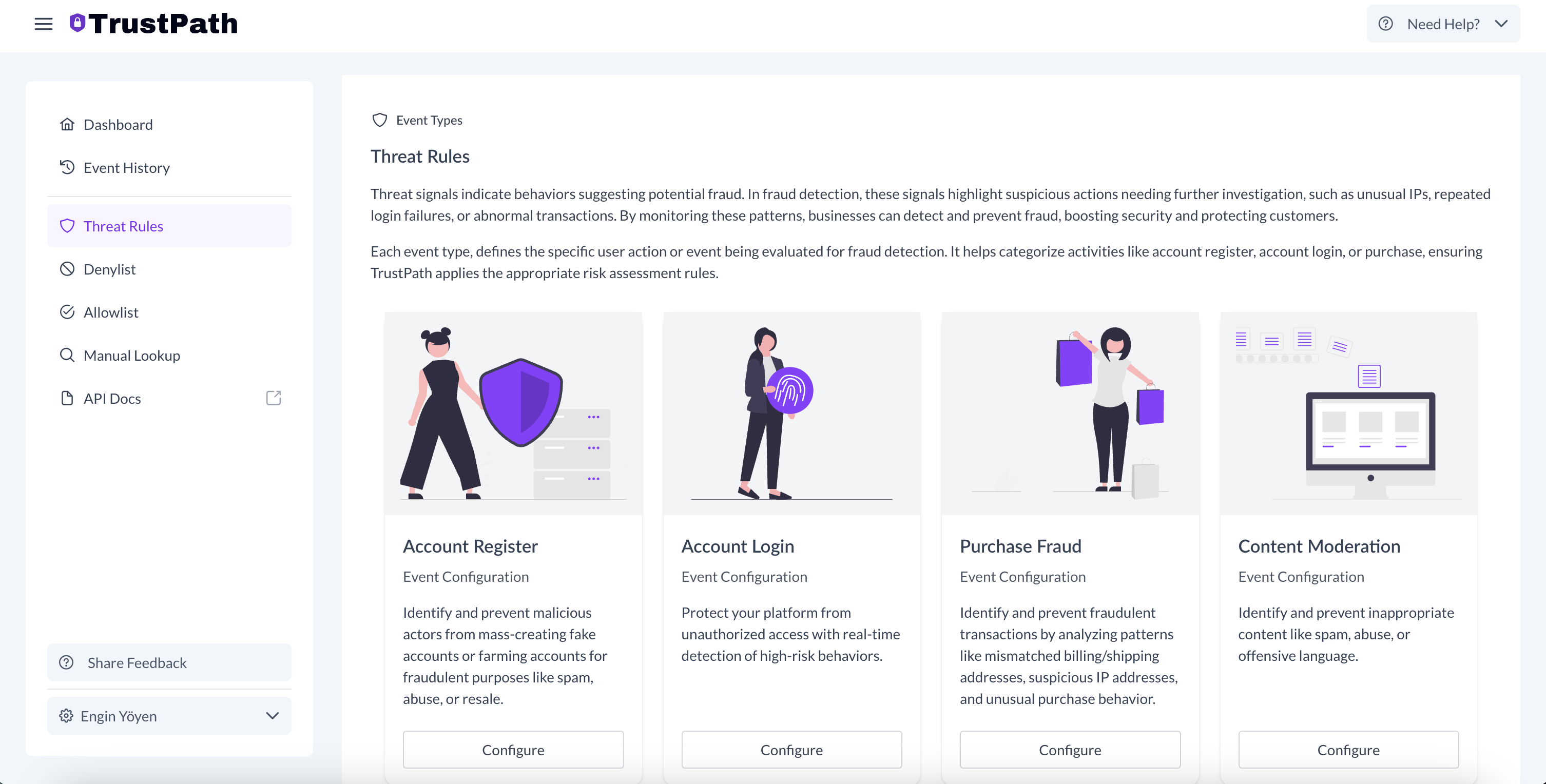
- Click the Navigate to the ThreatRules section in the dashboard.
- Select the Purchase Fraud card to begin configuration.
- TrustPath.io provides a set of default rules optimized for each event type, but you also have the flexibility to define custom rules based on your specific needs.
This setup allows you to tailor your risk scoring system and take automated action based on the threat level of each event.
Adding Rules to the order_purchase Event
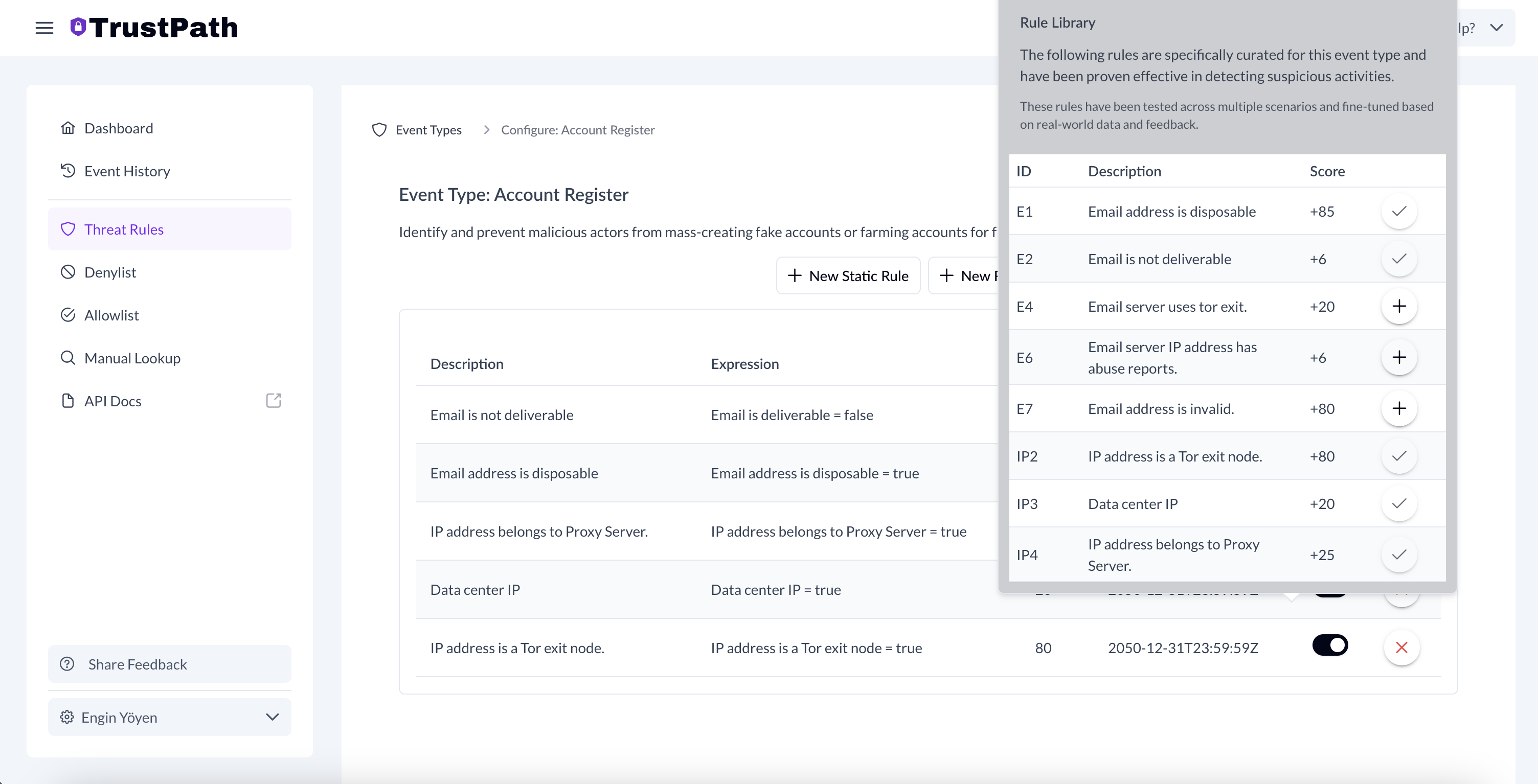
To enhance fraud detection during account registration, follow these steps:
-
Navigate to the AccountRegister event under ThreatRules.
-
Click on Add Rule From Library in the top-right corner.
-
From the list of available rules, select the following by simply clicking on each one:
- Email is not deliverable
- Email address is disposable
- IP address belongs to a Proxy Server
- Data center IP
- IP address is a Tor exit node
Once added, these rules will automatically trigger email and IP-based threat signal checks for every new account registration on your platform, improving your ability to catch spam and malicious signups in real time.
In this step, we're not just verifying whether the email address is disposable—we're also assessing the user's IP address for signs of suspicious activity. These additional checks significantly strengthen your platform's ability to detect and prevent fraudulent signups.
For instance, if a user's IP address is associated with a data center, proxy server, or a known Tor exit node, it often indicates attempts to mask identity or automate signups—both of which are common tactics used by malicious actors and bots. By incorporating these IP-based signals alongside email validation, you can more accurately flag high-risk signups and take action before any damage is done.