Prevent Signups Using Disposable or Spam Email Addresses
How to detect and prevent automated account creation and account farming
When it comes to protecting your SaaS platform from fraudulent activity, an email address can be one of the earliest indicators of user intent. Signups using disposable or suspicious email domains are often strongly correlated with spam, abuse, or automated bots. By analyzing key email-related signals, you can proactively block bad actors before they gain access to your platform. In this guide, we’ll walk through the essential Signals you can use to effectively reduce spam signups and keep your user base clean and trustworthy.
Prerequisites
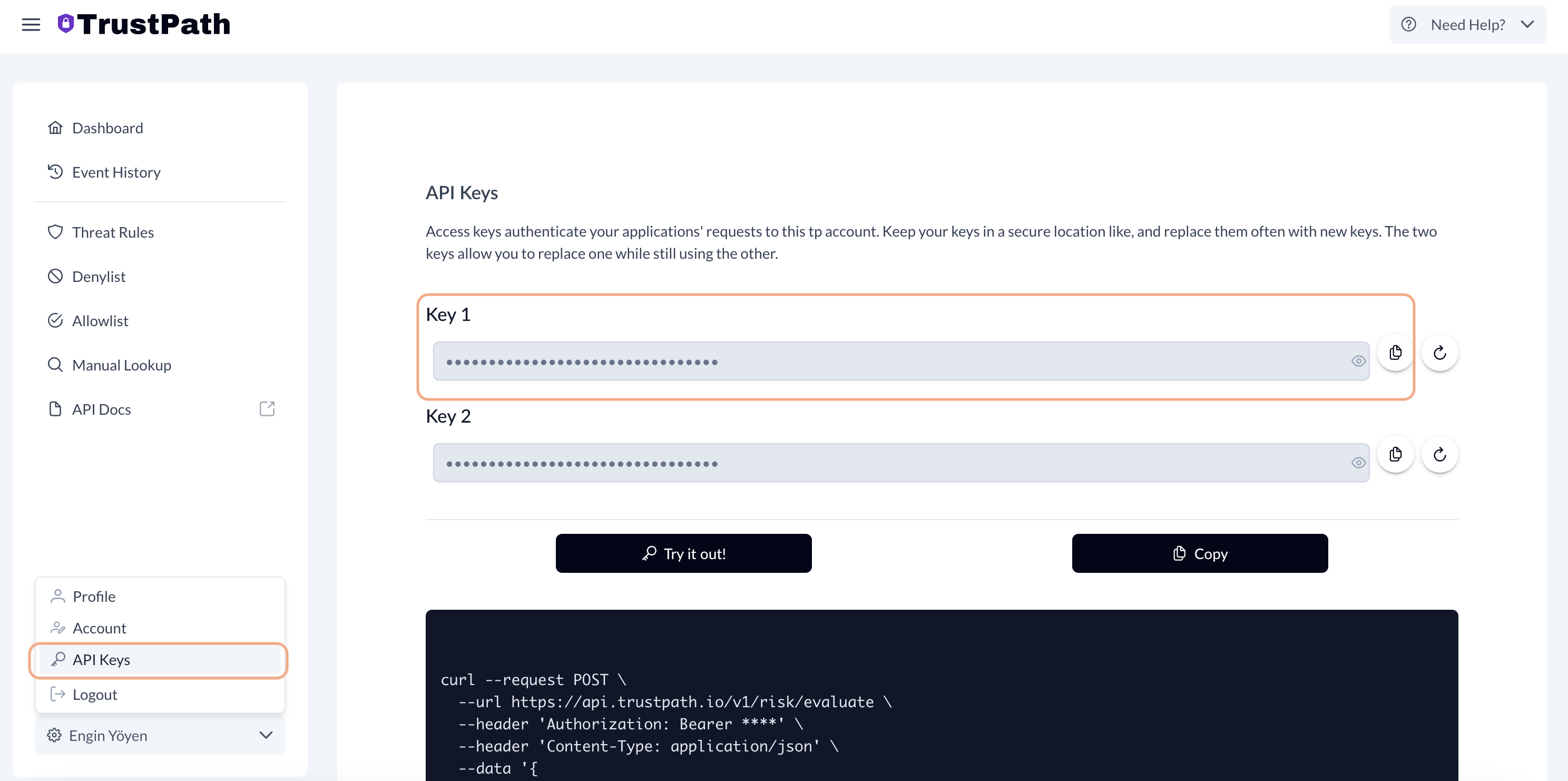
The first step is to create an account on TrustPath.io and obtain your API key.
- Go to https://trustpath.io and click on Sign In.
- Once registered, navigate to the API Key section from the lower-left menu.
- Copy your API key for use in your application.
Alternatively, you can copy the preconfigured curl request from the same page to test the system immediately.
TrustPath.io Threat Detection Rules
TrustPath.io threat detection rules are individual risk assessment criteria designed to identify and flag potentially fraudulent activity. Each rule evaluates specific signals—such as behavior patterns or metadata—to detect suspicious events and assigns a corresponding risk score.
The total risk score for an event ranges from 0 to 100, where:
- 0 indicates no risk (safe to approve)
- 100 indicates high risk (likely fraudulent, recommended to decline)
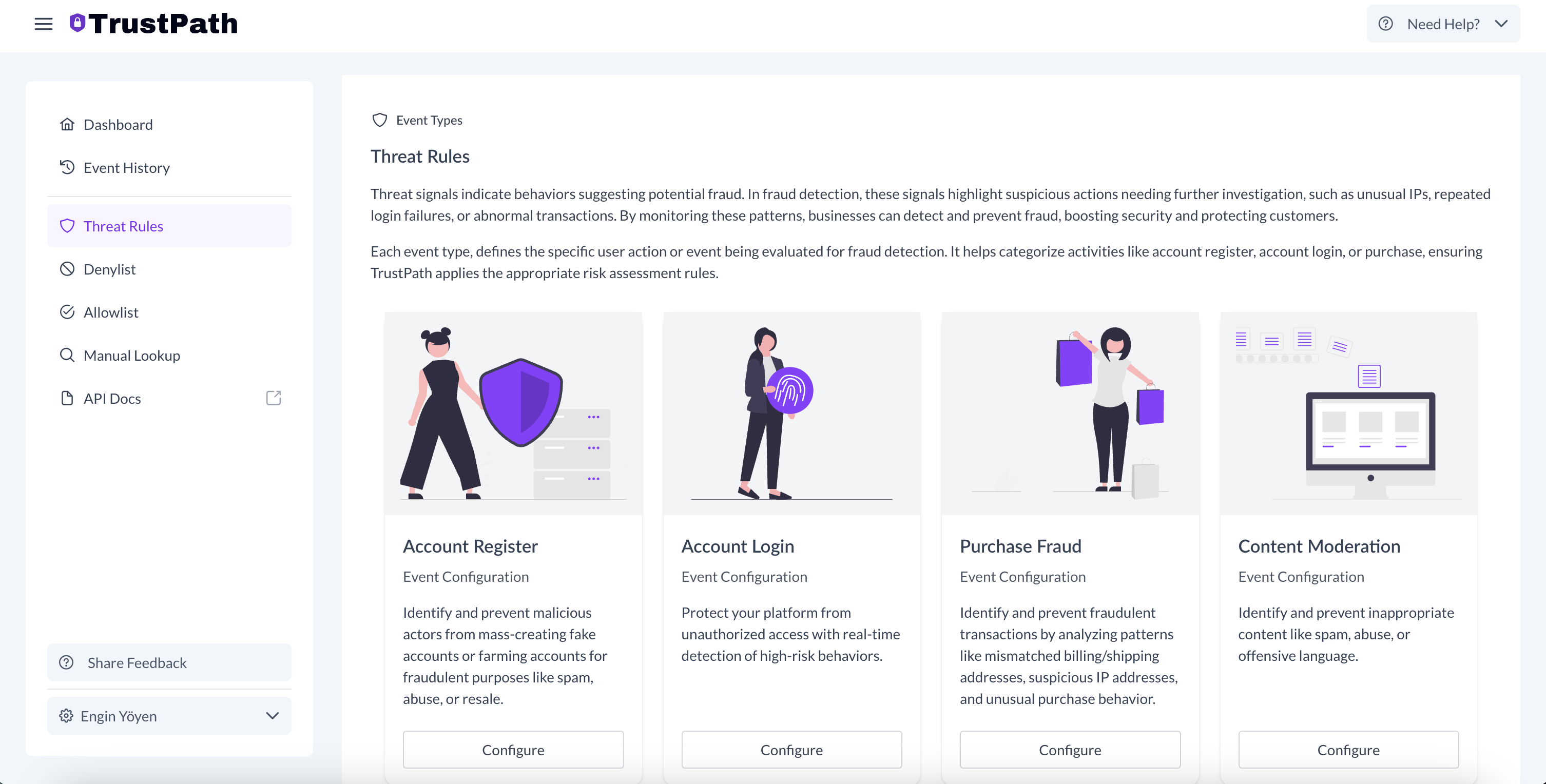
Setting Up account_register Event
To configure detection for account creation flows:
- Navigate to the ThreatRules section in the dashboard.
- Select the Account Register card to begin configuration.
- TrustPath.io provides a set of default rules optimized for each event type, but you also have the flexibility to define custom rules based on your specific needs.
This setup allows you to tailor your risk scoring system and take automated action based on the threat level of each event.
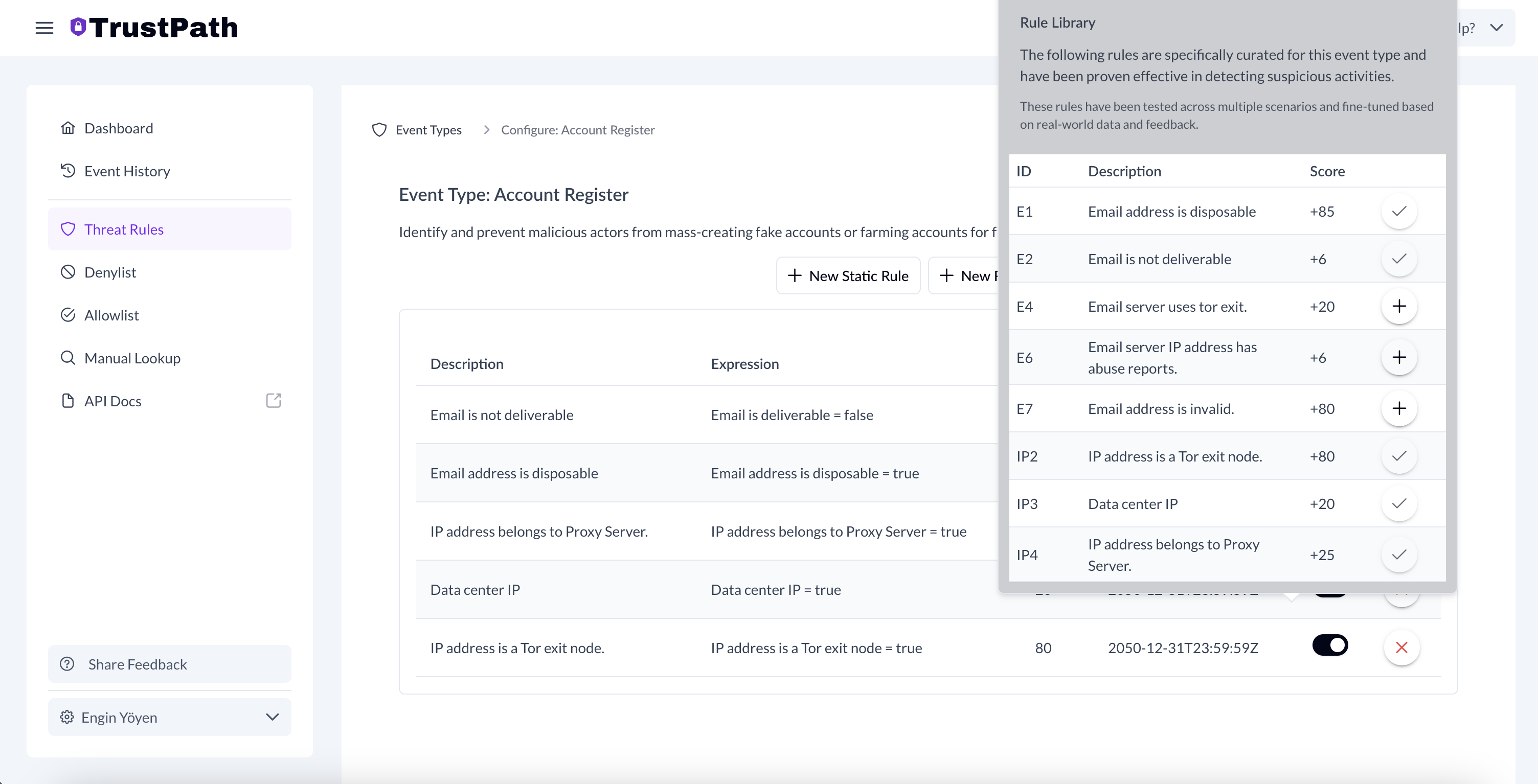
Adding Rules to the account_register Event
To enhance fraud detection during account registration, follow these steps:
-
Navigate to the AccountRegister event under ThreatRules.
-
Click on Add Rule From Library in the top-right corner.
-
From the list of available rules, select the following by simply clicking on each one:
- Email is not deliverable
- Email address is disposable
- IP address belongs to a Proxy Server
- Data center IP
- IP address is a Tor exit node
Once added, these rules will automatically trigger email and IP-based threat signal checks for every new account registration on your platform, improving your ability to catch spam and malicious signups in real time.
In this step, we’re not just verifying whether the email address is disposable—we’re also assessing the user's IP address for signs of suspicious activity. These additional checks significantly strengthen your platform's ability to detect and prevent fraudulent signups.
For instance, if a user’s IP address is associated with a data center, proxy server, or a known Tor exit node, it often indicates attempts to mask identity or automate signups—both of which are common tactics used by malicious actors and bots. By incorporating these IP-based signals alongside email validation, you can more accurately flag high-risk signups and take action before any damage is done.
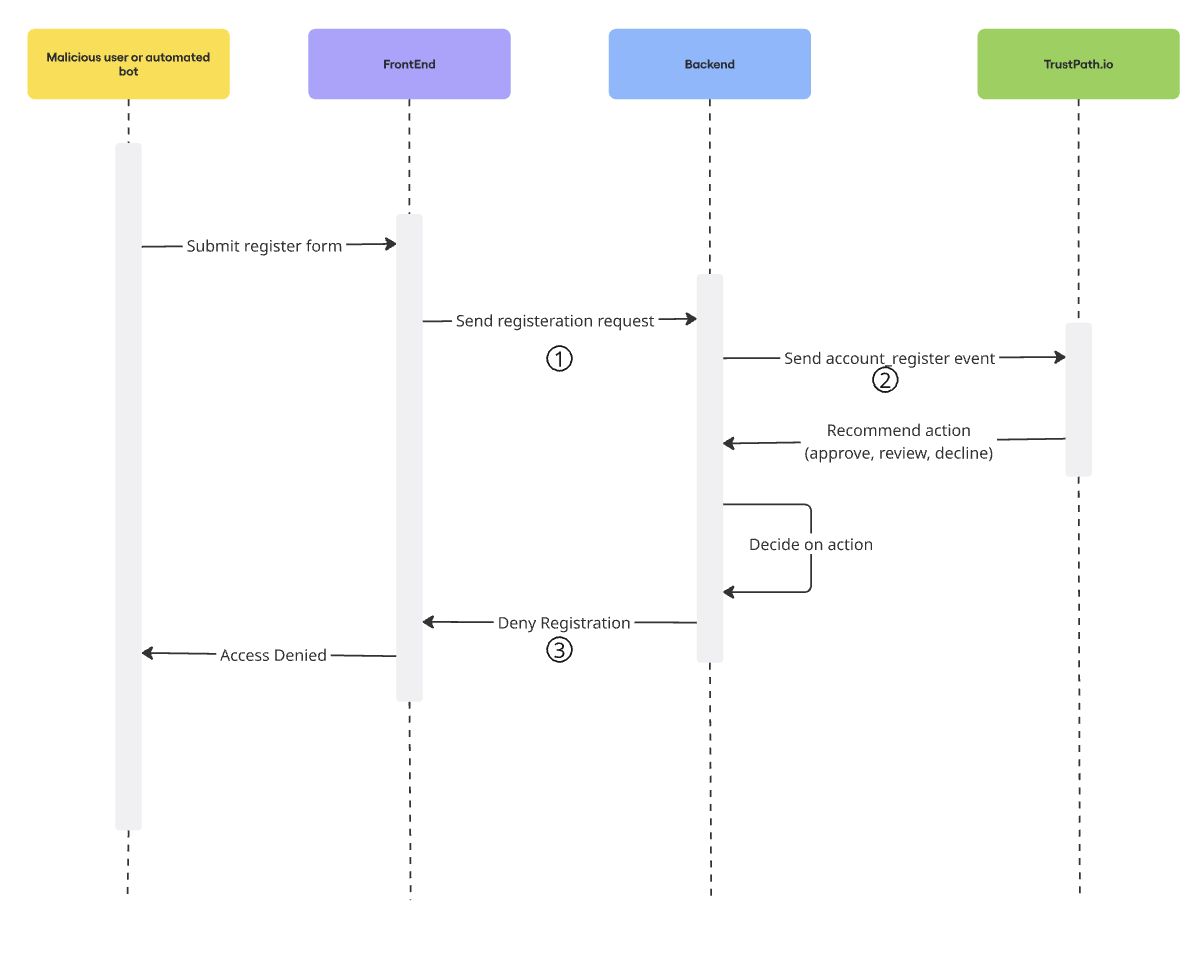
Integrating TrustPath.io with Your System
Now that everything is set up in TrustPath.io, the next step is to integrate it with your backend system.
The following flow diagram illustrates how this works:
When a malicious user or automated bot submits a registration form, the request first reaches your backend. Rather than immediately creating a new account, your backend sends a request to the TrustPath.io API, including the user's IP address and email.
TrustPath.io then enriches the incoming data and evaluates it against the threat detection rules you configured earlier. The response includes:
- A detailed breakdown of detected risks or issues
- A risk score between 0 and 100, which maps to a recommended action:
- 0–20: Approve
- 20–40: Review
- 40–100: Decline
Based on this response, your backend can then make an informed decision—whether to approve the registration, flag it for manual review, or block it entirely.
What the Request Looks Like
The following curl request highlights how straightforward the integration is.
To perform a threat assessment, simply include these three fields:
email– the user's email addressip– the user's IP addressevent_type– the type of event (e.g.,account_register)
curl --request POST \
--url https://api.trustpath.io/v1/risk/evaluate \
--header 'Authorization: Bearer API_KEY' \
--header 'Content-Type: application/json' \
--data '{
"ip": "85.22.116.1",
"email": "mail@disposable.com",
"event_type": "account_register"
}'
Understanding the Response
The response from TrustPath.io provides a rich set of data points, offering detailed insights into both the email and IP address. This includes:
- A list of triggered threat signals
- Email server validation details (e.g., deliverability, domain reputation)
- IP metadata such as ASN, geolocation, proxy status, and more
Below is a sample JSON response showcasing only the scoring section. In this example, TrustPath.io has detected that:
- The IP address belongs to a data center
- The IP is also identified as a Tor exit node
These high-risk indicators contribute to a total risk score exceeding 100, which is automatically capped at the maximum value of 100. As a result, the system returns a state of decline, indicating that the registration attempt should be blocked.
{
...
"score": {
"details": [
{
"rule_name": "Data center IP",
"rule_type": "static",
"score": 20
},
{
"rule_name": "IP address is a Tor exit node.",
"rule_type": "static",
"score": 80
}
],
"fraud_score": 100,
"state": "decline"
}
}
With this integration, you’re not only set up to prevent basic fraud like spam signups but also ready to tackle more advanced use cases. For example, you can leverage TrustPath.io to detect account sharing, where multiple users are accessing a single account from different locations or devices. Additionally, you can challenge users attempting to log in from new devices or unrecognized locations, enhancing your platform's security by validating their identity before granting access.